Here you’ll find a list of steganography tools. Before starting, it may be advisable to read some notes about this list.
Steganography in Images
- StegoApp [ PNG, JPG ]
- CryptoStego [ PNG, JPG ]
- F5 [ JPG ]
- HStego [ PNG, JPG ]
- JPHS [ JPG ]
- JSteg [ JPG ]
- OpenPuff [ BMP, JPG, PCX, PNG, TGA ]
- OpenStego [ PNG ]
- Outguess [ JPG ]
- SilentEye [ BMP, JPG ]
- SSuite Picsel [ BMP, PNG, JPG ]
- StegHide [ BMP, JPG ]
- QuickStego [ BMP, GIF, JPG ]
Steganography in Audio
- DeepSound [ FLAC, MP3, WAV, APE ]
- HiddenWave [ WAV ]
- MP3Stego [ MP3 ]
- OpenPuff [ AIFF, MP3, NEXT/SUN, WAV ]
- SilentEye [ WAV ]
- StegHide [ WAV, AU ]
Steganography in Video
- OpenPuff [ 3GP, MP4, MPG, VOB ]
Steganography in Text
Steganography in Other Media
- OpenPuff [ FLV, SWF, PDF ]
Notes About This List
This is a list of steganography tools that I am compiling. It includes a link where the tool can be obtained, a brief description, and a table indicating the operating systems it works on, the file types it works with, and the data embedding method it uses. The latter is especially important if you want to perform steganalysis using a tool like Aletheia.
Some data is still not available, usually because I have not found this information and have not yet had time to investigate the tool.
If you know some data that is not provided, or there is a tool that you think would be interesting to add to the list, you can get in touch with me here.
StegoApp
StegoApp is a steganography tool for images that runs in the browser.
| Operating System | Cross-platform (Web browser) |
| Image insertion method | Custom robust method |
| License | Free Tier with Premium Options |
Since this tool runs in the browser, it is only necessary to access the page and follow the instructions.
CryptoStego
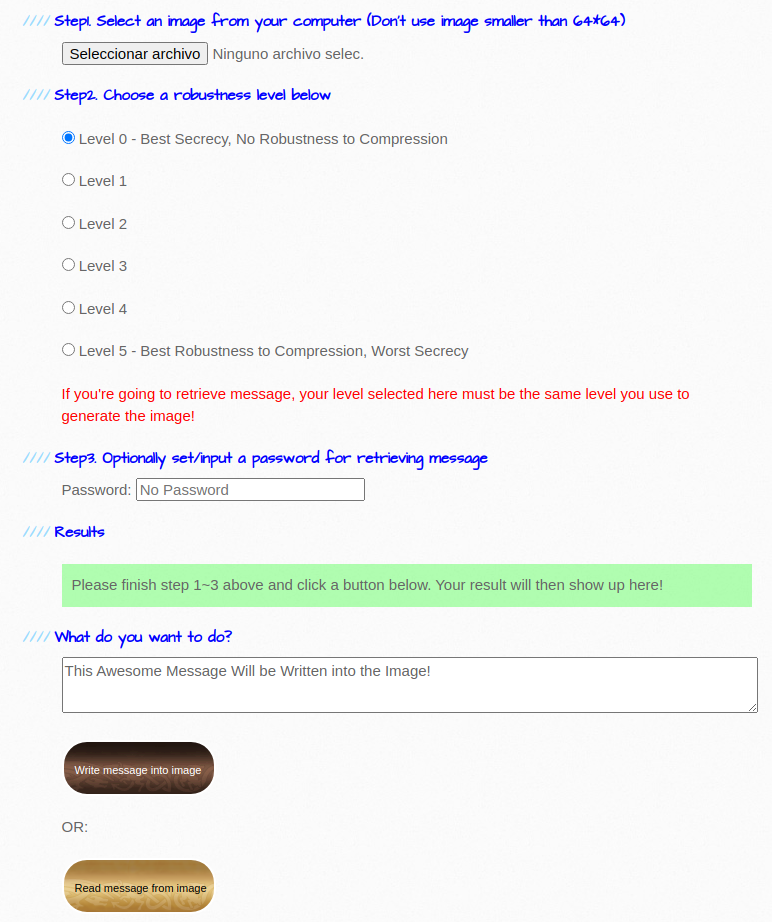
CryptoStego is a steganography tool for images that runs in the browser.
| Operating System | Cross-platform (Web browser) |
| Image insertion method | LSB Replacement |
| Image insertion method for JPG | Custom |
| License | MIT |
Since this tool runs in the browser, it is only necessary to access the page and follow the instructions.
ChatGPT
ChatGPT is an artificial intelligence model developed by OpenAI to simulate human conversations through text.
It is not a steganography tool per se, although its ability to generate high-quality texts allows it to be used as such. An example can be found in the article Text Steganography with ChatGPT.
DeepSound
DeepSound is a steganography tool that allows hiding information within audio files.
| Operating System | Windows |
| Supported Audio Formats | FLAC, MP3, WAV, APE |
| Audio Insertion Method | ? |
| License | Freeware |
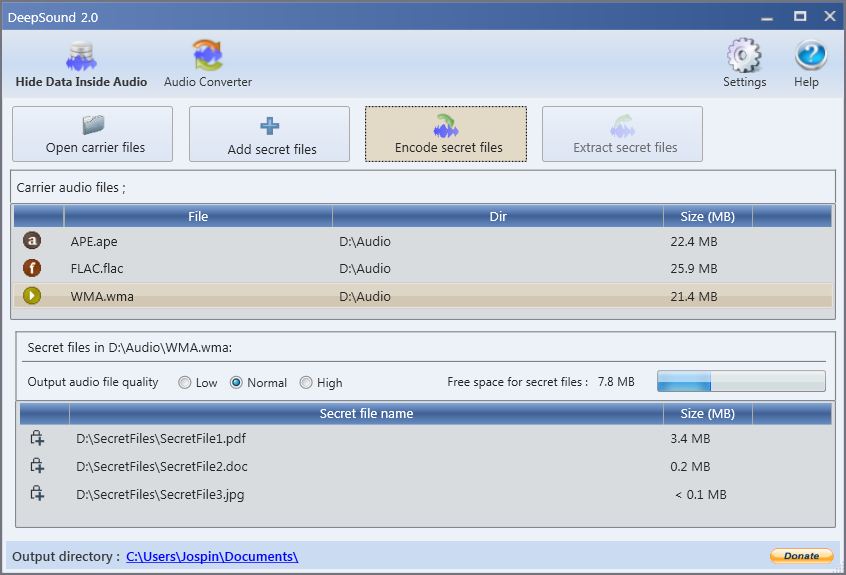
Graphical Interface:
DeepSound has a graphical interface that facilitates the hiding and extracting of information.
F5
F5 is a steganography tool for JPEG images.
| Operating System | Cross-platform (Java) |
| JPG Image Insertion Method | Custom |
| License | MIT |
Embedding a message using commands:
To hide a “secret.txt” file in a cover image, we can use the following command:
java -jar f5.jar e -p p4ssw0rd -e secret.txt cover.jpg stego.jpg
Extracting a message using commands:
To extract hidden information from a stego image, we can use the following command:
java -jar f5.jar x -p p4ssw0rd -xf output.txt stego.jpg
HiddenWave
HiddenWave is a steganography tool for audio in WAV files.
| Operating System | Cross-platform (Python) |
| WAV Audio Insertion Method | LSB replacement |
| License | Public Domain / Unlicensed |
Embedding a message using commands:
To hide a message in a cover audio we can use the following command:
python3 HiddenWave.py -f cover.wav -m "Secret message" -o stego.wav
Extracting a message using commands:
To extract hidden information from the stego audio we can use the following command:
python3 ExWave.py -f stego.wav
HStego
HStego is a steganography tool that allows hiding information in PNG and JPG images. The main objective of this tool is to go undetected by modern steganalysis tools.
| Operating System | Windows, Linux |
| Supported Formats | PNG, JPG |
| Image Insertion Method | STC + S-UNIWARD |
| JPG Image Insertion Method | STC + J-UNIWARD |
| License | MIT |
Embedding a message using commands:
To hide a “secret.txt” file in a cover image, we can use the following command:
hstego.py embed secret.txt cover.png stego.png p4ssw0rd
Extracting a message using commands:
To extract hidden information from a stego image, we can use the following command:
hstego.py extract stego.png content.txt p4ssw0rd
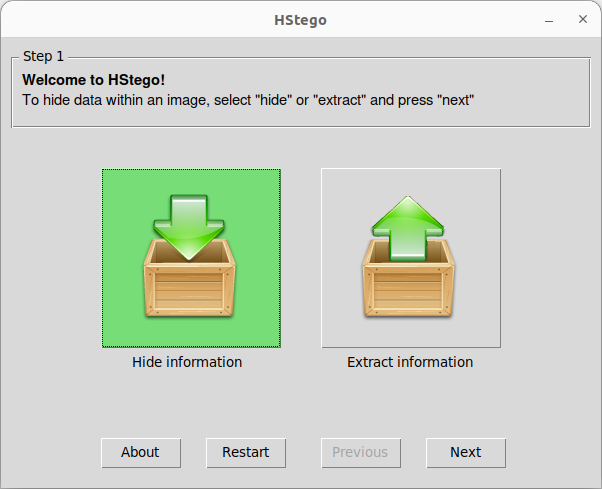
Graphical Interface:
The HStego tool has a graphical interface that allows hiding and extracting information, as well as embedding and verifying watermarks.
JPHS
JP Hide & Seek is a steganography tool for JPEG images.
| Operating System | Linux |
| JPG Image Insertion Method | DCT LSB replacement |
| License | GPL v2 |
Embedding a message using commands:
To hide a “secret.txt” file in a cover image, we can use the following command:
jphide cover.jpg stego.jpg secret.txt
Extracting a message using commands:
To extract hidden information from a stego image, we can use the following command:
jpseek stego.jpg output.txt
JSteg
JSteg is a steganography tool for JPEG images.
| Operating System | Linux |
| JPG Image Insertion Method | DCT LSB replacement (ignores values 0 and 1) |
| License | Custom license similar to BSD |
Embedding a message using commands:
To hide a “secret.txt” file in a cover image, we can use the following command:
cjpeg -steg secret.txt cover.pgm > stego.jpg
Extraction of a message using commands:
To extract hidden information in a stego image, we can use the following command:
djpeg -steg output.txt stego.jpg > out.jpg
MP3Stego
MP3Stego is a steganography tool that hides information during the compression of a WAV file to MP3.
| Operating System | Windows |
| Insertion Method for MP3 Audio | Custom |
| License | ? |
Embedding a message using commands:
To hide a “secret.txt” file in a cover audio file, we can use the following command:
encode -E secret.txt -P p4ssw0rd cover.wav stego.mp3
Extracting a Message Using Commands:
To extract hidden information from the stego audio, we can use the following command:
decode -X -P p4ssw0rd svega_stego.mp3
OpenPuff
OpenPuff is a steganography tool that allows the hiding of information in multiple formats.
| Operating System | Windows, Linux |
| Supported Image Formats | BMP, JPG, PCX, PNG, TGA |
| Supported Audio Formats | AIFF, MP3, NEXT/SUN, WAV |
| Supported Video Formats | 3GP, MP4, MPG, VOB |
| Other Supported Formats | FLV, SWF, PDF |
| Image Insertion Method | LSB replacement |
| JPEG Image Insertion Method | Steghide? |
| Video Insertion Method | ? |
| Other Formats Insertion Method | ? |
| License | LGPL v3 + Partially closed code |
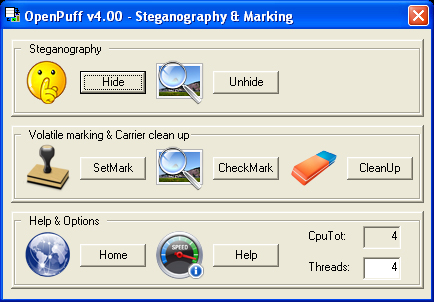
Graphical Interface:
The OpenPuff tool has a graphical interface that allows hiding and extracting information, as well as embedding and verifying the watermark.
OpenStego
OpenStego is a steganography tool for images, which allows the hiding of information both for the transmission of secret messages and for watermarking.
| Operating System | Cross-platform (Java) |
| Supported Formats | PNG |
| Insertion Method | LSB replacement |
| License | GPL v2 |
Embedding a message using commands:
To hide a file “secret.txt” inside a cover image we can use the following command:
java -jar openstego.jar embed -a randomlsb -mf secret.txt -cf cover.png -sf stego.png
Extracting a message using commands:
To extract hidden information from a stego image we can use the following command:
java -jar openstego.jar extract -a randomlsb -sf stego.png -xd output-dir
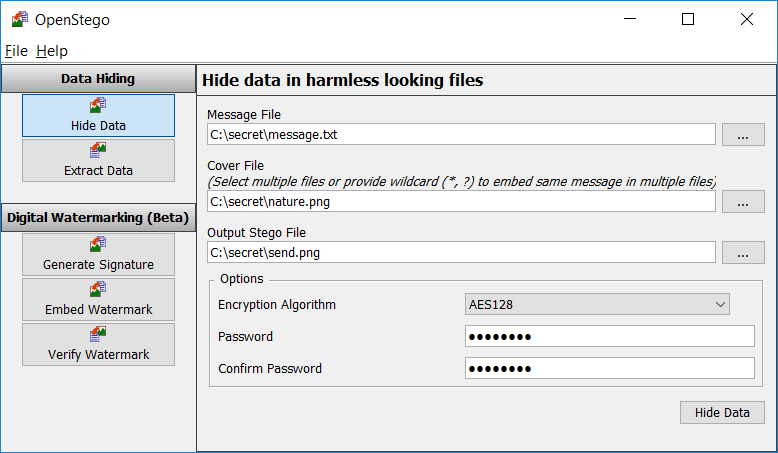
Graphical Interface:
The OpenStego tool has a graphical interface that allows hiding and extracting information, as well as embedding and verifying the watermark.
Outguess
Outguess is a steganography tool for JPEG images.
| Operating System | Linux |
| JPEG Images Insertion Method | Custom |
| License | MIT |
Embedding a message using commands:
To hide a file “secret.txt” inside a cover image we can use the following command:
outguess -k p4ssw0rd -d secret.txt cover.jpg stego.jpg
Extracting a message using commands:
To extract hidden information from a stego image we can use the following command:
outguess -k p4ssw0rd -r stego.jpg output.txt
QuickStego
QuickStego is a steganography tool that allows hiding information in images.
| Operating System | Windows |
| Supported Formats | BMP, GIF, JPG |
| Image Insertion Method | ? |
| JPEG Image Insertion Method | ? |
| License | Freeware |
Graphical Interface:
The QuickStego tool has a graphical interface that allows hiding and extracting information.
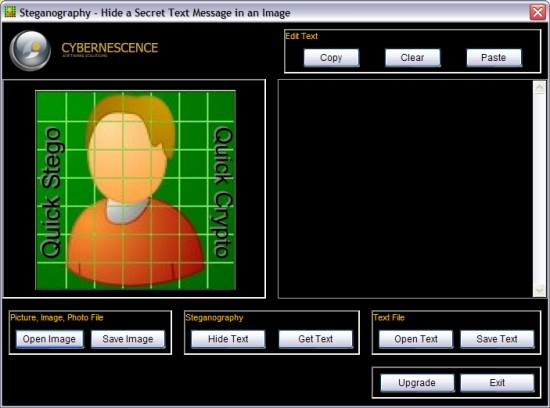
SilentEye
SilentEye is a steganography tool that allows hiding information in images and audio.
| Operating System | Windows, MacOS X, Linux |
| Supported Formats | BMP, WAV |
| Image Insertion Method | LSB replacement |
| JPEG Image Insertion Method | ? |
| Audio Insertion Method | ? |
| License | GPL v3 |
Graphical Interface:
The SilentEye tool has a graphical interface that allows hiding and extracting information.
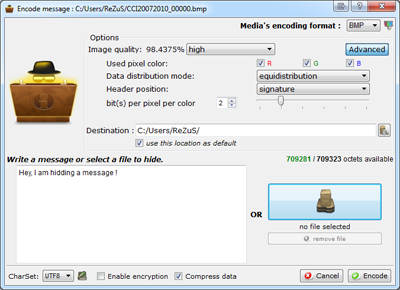
SSuite Picsel
SSuite Picsel is a steganography tool that allows hiding information in images.
| Operating System | Windows, MacOS X, Linux |
| Supported Formats | BMP, PNG, JPG |
| Image Insertion Method | ? |
| JPEG Image Insertion Method | ? |
| License | Freeware |
Graphical Interface:
The SSuite Picsel tool has a graphical interface that allows hiding and extracting information.
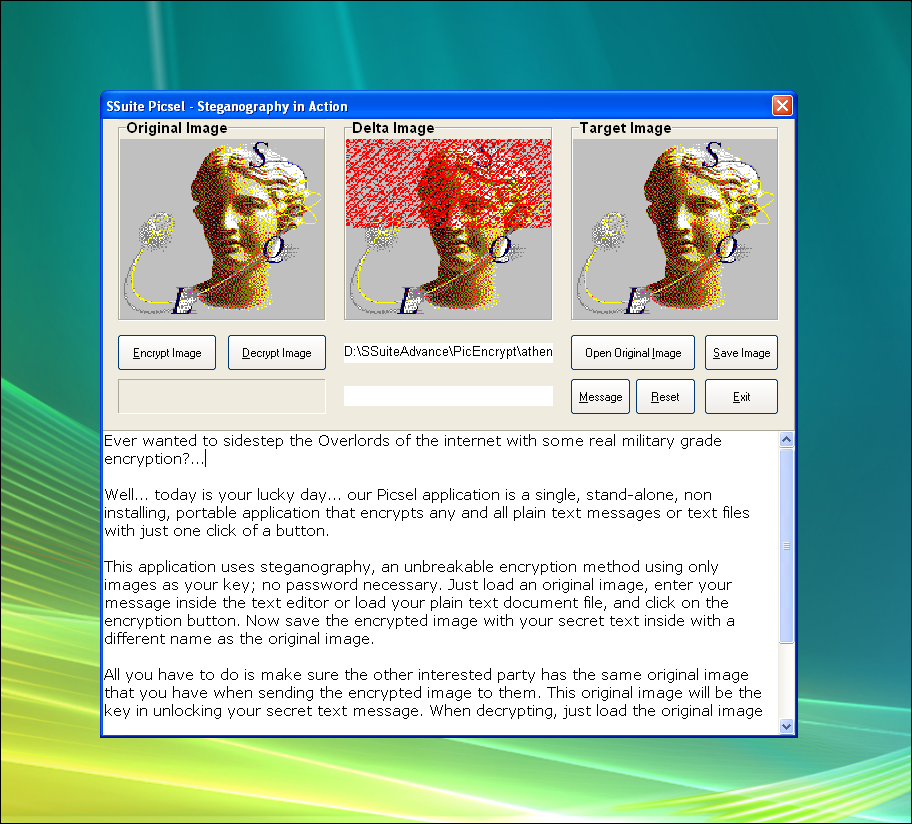
Steg
Steg is a steganography tool that allows hiding information in ASCII text using different encodings for whitespace.
| Operating System | Cross-platform (D) |
| Insertion Method for Text | Spaces with different encodings |
| License | GPL v3 |
Embedding a message using commands:
To hide a message inside a cover image we can use the following command:
steg -c cover.txt -o stego.txt "This is a message"
Extracting a message using commands:
To extract hidden information from a stego text we can use the following command:
steg -d -s stego.txt
Steghide
Steghide is a steganography tool that allows hiding information in images and audio.
| Operating System | Windows, Linux |
| Supported Formats for Images | BMP, JPG |
| Supported Formats for Audio | WAV, AU |
| Insertion Method for Images | Custom |
| Insertion Method for JPG Images | Custom |
| Insertion Method for Audio | Custom |
| License | GPL v2 |
Embedding a message using commands:
To hide a file “secret.txt” inside a cover image we can use the following command:
steghide embed -cf cover.jpg -ef secret.txt -sf stego.jpg -p p4ssw0rd
Extracting a message using commands:
To extract hidden information from a stego image we can use the following command:
steghide extract -sf stego.jpg -xf output.txt -p p4ssw0rd -f
There are currently no comments on this article.
Add a Comment